Um relatório recente de pesquisadores da Avast identificou um malware antigo chamado GuptiMiner. Ele usa o mecanismo de atualização do Antivírus do Esca para furtiva Injetar backdoors e programas de mineração de criptomoedas em usuários’ sistemas de computador e grandes redes corporativas. Isso é mais uma evidência de que os cibercriminosos estão adaptando suas técnicas para ignorar as medidas de segurança modernas. Vejamos a situação.
Descoberta de campanha e Guptiminer
Os especialistas do Avast analisaram a atividade do malware Guptiminer ativo desde 2018. Guptiminer é um malware sofisticado que visa espalhar backdoors e executar criptografia oculta em redes corporativas. O malware utiliza uma cadeia de infecções de vários estágios. Começa com seqüestrando atualizações de software antivírus Através do homem no meio (MitM) ataques. Isso permite que os invasores substituam atualizações legítimas por maliciosas.
Avast informou escan e certificado de Índia de a vulnerabilidade encontrada, que foi corrigido com sucesso em julho 31, 2023. No entanto, Como os usuários raramente instalam mais de um antivírus, Isso limita a capacidade de detectar e analisar todo o escopo das atividades de Guptiminer.
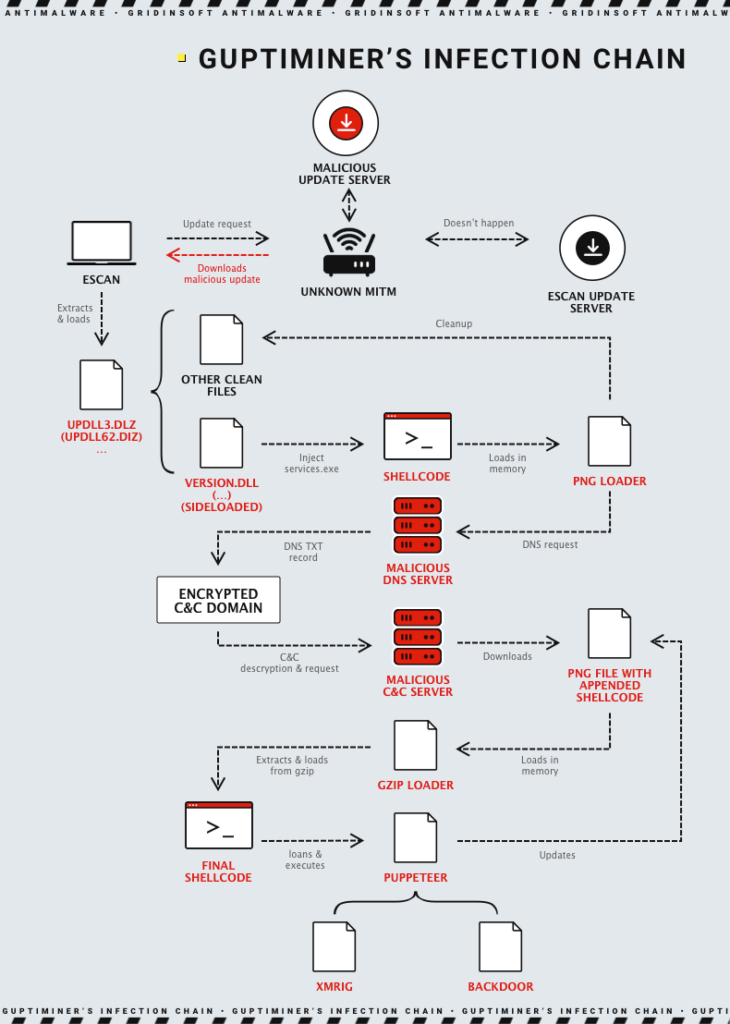
Este malware usa uma cadeia de infecção complexa. O ataque começa interceptando as atualizações do Antivírus Escan. O programa de atualização é baixado do servidor, Mas em seu caminho é um atacante que o substitui por um malicioso. Próximo, O ESCAN descomprima e baixa o pacote, Iniciando uma cadeia de infecção usando uma DLL. Esta DLL permite que o vírus controla mais downloads e execução de código.
Próximo, Guptiminer usa uma técnica de carga lateral para injetar código malicioso em processos confiáveis, que permite que o programa permaneça invisível para os sistemas antivírus. O malware também se comunica com remoto comando e controle (C2) servidores Para receber comandos e atualizações. Isso permite que os invasores controlem sistemas infectados, Execute processos maliciosos adicionais, ou realizar mineração de criptomoeda.
Como funciona o Guptiminer?
A análise Guptiminer revelou que o malware usou uma variedade de técnicas sofisticadas para instalar e ocultar sua presença no sistema. As principais técnicas incluíram DLL de mar, modificando arquivos do sistema, e usando assinaturas digitais forjadas para simular a legitimidade.
Também, Uma das características características do Guptiminer é sua capacidade de modularizar infecções. Isso inclui Executando consultas DNS nos servidores DNS do atacante e extrair dados úteis de imagens de aparência inocente. Além de sua funcionalidade principal de instalando backdoors, Guptiminer espalhe inesperadamente o mineiro XMRIG usado para extrair a criptomoeda do monero.
O processo de atribuição dinamicamente de tópicos de mineração para XMRIG:
xmrig_shellcode_copy_ = xmrig_shellcode_copy;
num_cores_ = num_cores;
dword_140020908 = 25;
xmrig_shellcode_copy-›max_cpu_usage = '53';
xmrig_shellcode_copy_->threads = '1';
if (num_cores_ >= 6)
xmrig_shellcode_copy_-›threads = '2';
if ( num_cores_ >= 8 )
xmrig_shellcode_copy_->threads = '3';
O malware foi identificado como potencialmente ligado ao Kimsuky, Um proeminente grupo de hackers norte -coreano. Isso indica possível patrocínio estadual e um alto grau de organização dos ataques. Antes, Hackers norte -coreanos mostraram um certo grau de interesse em adquirir criptomoeda. Então, Isso não deve ser uma surpresa demais.
Dois tipos diferentes de backdoors
Ao analisar o malware Guptiminer, Os pesquisadores identificaram dois diferentes tipos de backdoors. Ambos os tipos de backdoors foram projetados para funcionar como parte de uma campanha em larga escala e bem planejada. Mas cada um foi projetado para executar tarefas específicas em redes corporativas infectadas.
- O primeiro tipo de backdoor é uma versão modificada do link de Putty, que é usado para escanear pequenas etapas na rede local. Este backdoor permite o movimento lateral (Propagação horizontal de malware dentro da rede) para Acesse sistemas potencialmente vulneráveis Executando janelas 7 e Windows Servidor 2008. Isso facilita a exploração de vulnerabilidades em sistemas operacionais legados.
- O segundo tipo de backdoor é multifuncional e modular. Ele aceita comandos do invasor para instalar módulos adicionais e especializado em encontrar e roubar chaves privadas armazenadas localmente e carteiras de criptomoedas. Essa abordagem permite que os invasores monitorem sistemas infectados por longos períodos de tempo e ativam recursos maliciosos adicionais, se necessário.


