Segurança para celulares
Microsoft warns of dangerous vulnerability in Surface Pro 3 devices
Os engenheiros da Microsoft publicaram um boletim de segurança sobre uma nova vulnerabilidade que afeta o Surface Pro 3 comprimidos. The bug could be…
Ukrainian cyber police arrested ransomware operators who “earned” $150 million
A Polícia Cibernética Ucraniana prendeu dois operadores de um ransomware não identificado. It is reported that the operation was carried out…
Experts showed fraudulent payments from a locked iPhone with Apple Pay and a Visa card
Scientists talked about how to make fraudulent payments using Apple Pay with a Visa card on a locked iPhone. Esse…
Encryption algorithms for 2G networks have been intentionally weakened
A group of scientists from several European universities published a report on encryption algorithms for 2G networks, which many information…
Google stopped trying to shorten URLs in the address bar
A experiência do Google com tentativa de encurtar URLs (ocultando partes do URL da barra de endereço) has finally failed and…
Microsoft urges users to opt out of multi-factor authentication via phone
Microsoft experts have once again raised the issue of the…
Platypus attack allows stealing data from Intel processors
Um grupo de cientistas da Universidade Técnica de Graz…
Experts discovered that many mobile browsers are vulnerable to url spoofing
Rapid7 analysts and independent information security expert Rafay Baloch discovered…
MalLocker ransomware easily tricks Russians, pretending to be a screen lock from the police
Especialistas da Microsoft falaram sobre o novo ransomware Android AndroidOS/MalLocker. (doravante…
Cellmate men’s chastity belts are vulnerable to attacks and dangerous for users
Os analistas da Pen Test Partners estudaram um dispositivo extremamente incomum:…
Google recruits a team of experts to find bugs in Android applications
ZDNet relata que uma série de novas posições foram…
Attackers can bypass TikTok multi-factor authentication through the site
Jornalistas da publicação ZDNet, citando um de seus leitores,…
Microsoft left open one of the internal servers of the search engine Bing
Ata Hakcil, especialista em segurança cibernética na WizCase, descobriu que a Microsoft…
SpiKey technique allows opening the lock by recording a sound of a turning key
Cientistas da Universidade Nacional de Singapura publicaram um…
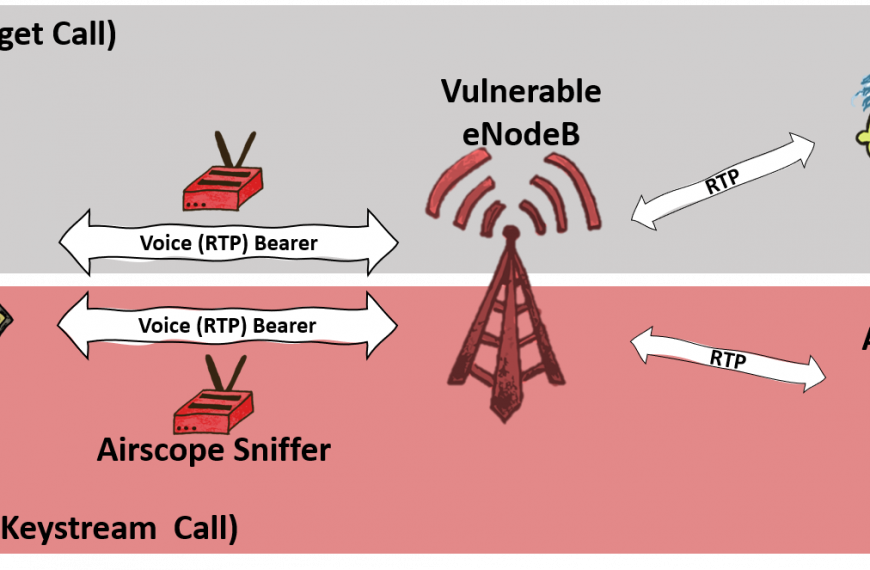
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Especialistas da Universidade do Ruhr e da Universidade de Nova York em…
Citrix expects attacks on fresh issues in XenMobile
Os engenheiros da Citrix lançaram vários patches do Citrix Endpoint Management…
Media Reports that Garmin Paid Ransom to WastedLocker Malware Operators
Em julho 2020, Garmin, o fabricante de eletrônicos vestíveis e…