Notícias, Pontas, Laboratório de segurança
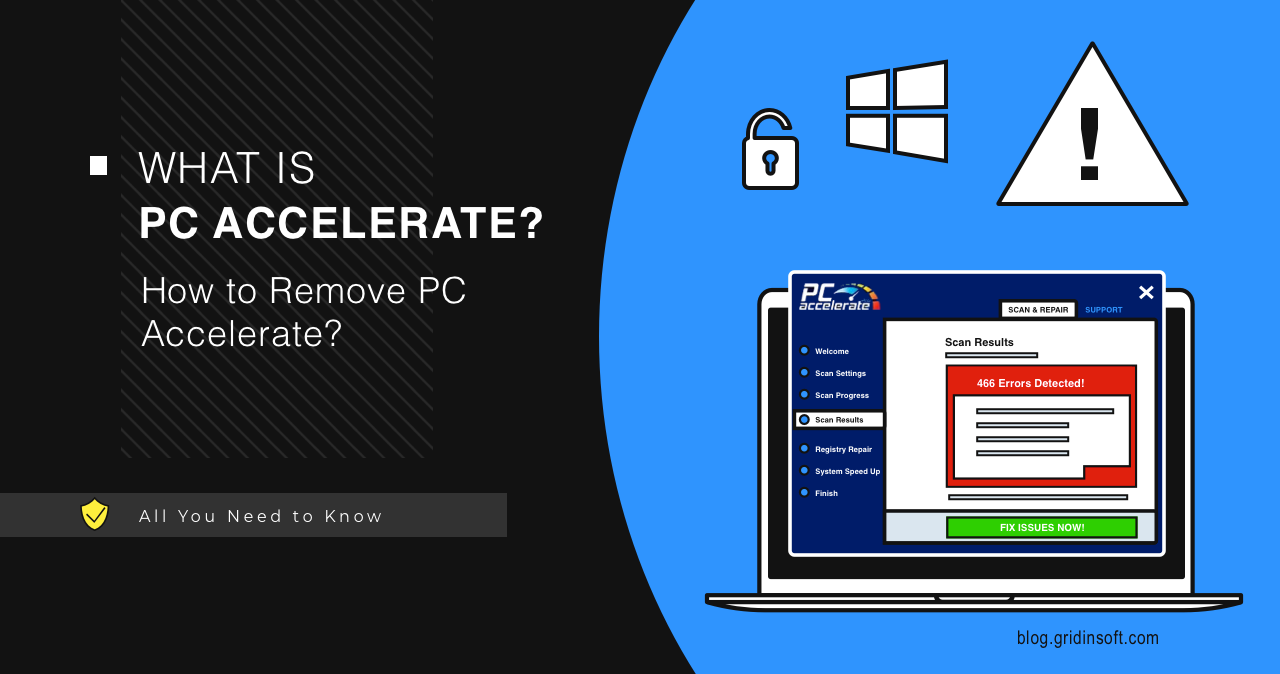
PC Accelerate
PC Accelerate é um software questionável que se apresenta como um utilitário útil projetado para otimizar o desempenho do seu computador. Em…
Virus:Win32/Floxif.H
Virus:Win32/Floxif.H é uma detecção de um programa malicioso, though not a virus as you may suppose by its name. Programas maliciosos…
HxTsr.exe – What is the HxTsr Process?
The HxTsr.exe process is a part of the Microsoft Outlook Communications component of the Windows 10/11 sistema operacional. Este processo…
PUA:Win32/Caypnamer.A!ml
PUA:Win32/Caypnamer.A!ml is a detection used by Microsoft’s Defender that identifies files or processes exhibiting suspicious characteristics. It is typically associated…
URL:Scam (Avast)
URL:Scam é um nome genérico de detecção de um site perigoso, que aparece em vários mecanismos antivírus. It may appear during…
PUABundler:Win32/PiriformBundler
PUABundler:Win32/PiriformBundler é a detecção de um programa indesejado, developed and…
Novice Rugmi Loader Delivers Various Spyware
The threat landscape meets a new player – Rugmi Loader.…
Xamalicious Trojan Hits Over 327K Android Devices
Um novo backdoor para Android, apelidado de Xamalicious, was discovered by the…
Integris Health Hacked, Patients Receive Ransom Emails
Integris Saúde, A mais extensa rede de saúde sem fins lucrativos de Oklahoma, fell victim…
Carbanak is Back with a New Spreading Tactic
O grupo de crimes cibernéticos Carbanak, famoso por seu malware bancário, tem…
What Should You Do When You Get Scammed?
À medida que as fraudes online se tornam não só mais difundidas, mas também…
What are Crypto Draining Attacks? Signs & Mitigation
Entre uma grande variedade de possíveis golpes que envolvem criptomoedas,…
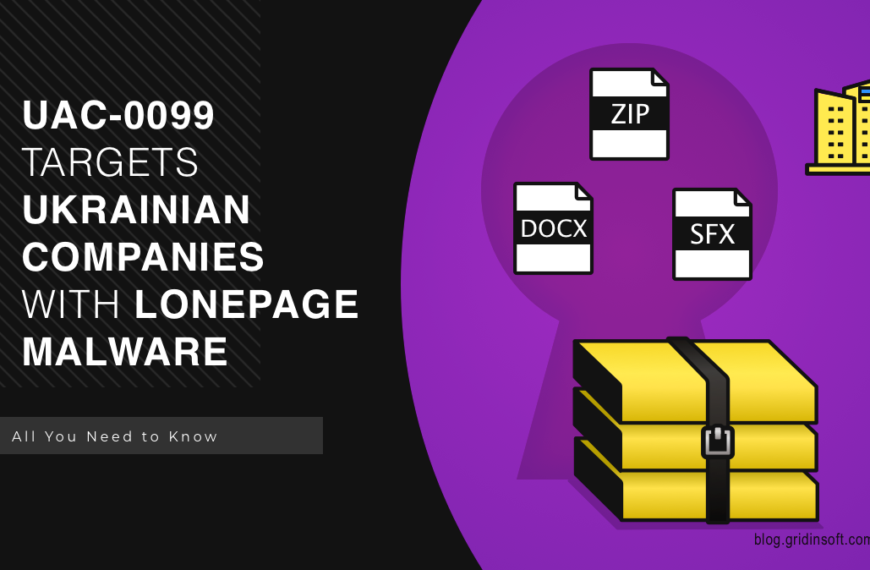
UAC-0099 Targets Ukrainian Companies With Lonepage Malware
Ukrainian cyberwarfare sees further action as the UAC-0099 threat actor…
FalseFont Malware Targets Defence Contractors Worldwide
The Iranian hacking group APT33 has developed a new malware…
Cryptocurrency Scams on Twitter Exploit Post Features
Fraudsters are seen to exploit a feature of Twitter publications,…
What are Remote Encryption Attacks? Explanation & Mitigation
The digital world is seeing a surge in remote encryption…
Comcast’s Xfinity Breach Exposes Data of 35.8 Million Users
Comcast confirms a massive security breach impacting its Xfinity division.…