Notícias, Pontas, Laboratório de segurança
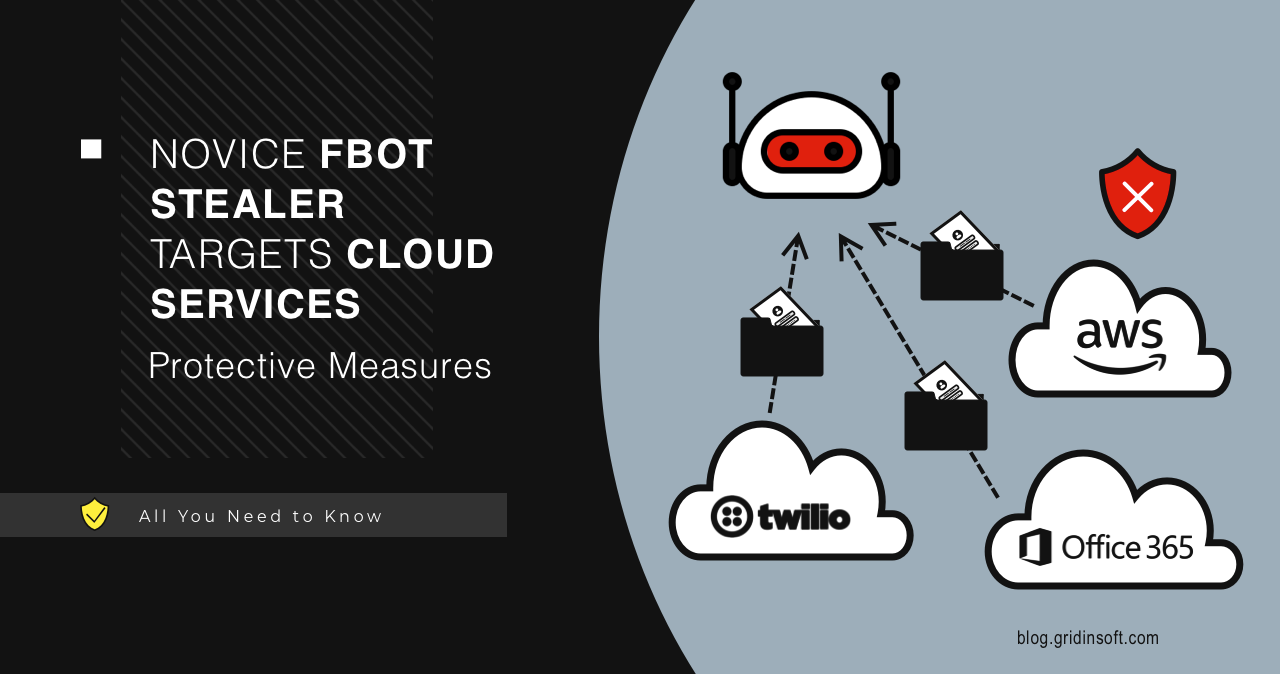
Novice FBot Stealer Targets Cloud Services
Pesquisadores relatam sobre uma nova cepa de malware chamada FBot. This Python-based malicious program appears to be a unique tool in…
AzorUlt Stealer Is Back In Action, Uses Email Phishing
Especialistas em segurança cibernética encontraram o malware Azorult de oito anos. Este malware rouba informações e coleta dados confidenciais, and has been…
Remcos RAT Targets South Korean Users Through Webhards
An infamous Remcos RAT reportedly started targeting South Korean users through the files shared on Webhards platform. By baiting users…
GitLab Zero-Click Account Hijack Vulnerability Revealed
Em janeiro 11, 2024, GitLab lançou uma atualização com o aviso oficial sobre a correção de violação crítica de segurança. A vulnerabilidade…
Windows SmartScreen Vulnerability Exploited to Spread Phemedrone Stealer
The malicious campaign exploits the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen to spread Phemedrone Stealer. It utilizes intricate evasion…
PaperCut Vulnerability Allows RCE, Exploited in the Wild
Corte de papel, uma solução de software usada para gerenciamento de impressão, appears to…
New SLP Vulnerability Allows 2200x DDoS Amplification
Uma vulnerabilidade recentemente descoberta no SLP, um protocolo de rede legado, pode…
Supply Chain Attack Leads to 3CX Hack and Other Supply Chain Attacks
An investigation into a supply chain attack that hit 3CX…
Capita Hacked, Black Basta Gang Publishes Data
capitão, uma empresa internacional de terceirização de processos de negócios com sede em Londres, foi hackeado…
Medusa Groups Claims That It “Merged” the Source Code of Bing and Cortana into the Network
Medusa extortionist group claims to have published internal materials stolen…
Chinese Hackers Use Google Command & Control Capabilities in Attacks
Especialistas do Google alertaram que os chineses “governo” hackear grupo…
5 Signs That You’ve Fallen Victim to a Scam
A fraude na Internet está se tornando cada vez mais difundida e sofisticada. From simple…
Legion Hacker Tool Used to Steal Data from Poorly Protected Websites
Experts have discovered a Python-based Legion hacking tool that is…
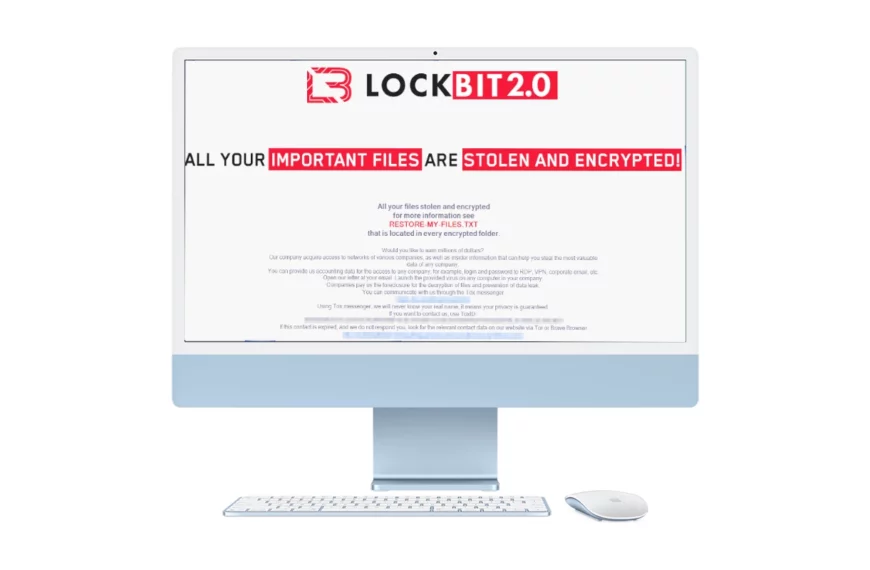
LockBit Releases World’s First macOS Ransomware
Bloqueio, an infamous ransomware gang that became a major threat…
Domino Backdoor is Lead by FIN7 and Conti Actors
Um novo Domino Backdoor apareceu no início de…
Can PDFs Have Virus? Exploring the Risks of Downloading PDF Files
Entre vários outros arquivos, PDFs are considered one of the…
Microsoft Told How to Detect the Installation of the BlackLotus UEFI Bootkit
Microsoft has shared a guide to help organizations detect the…