O blog de segurança da Gridinsoft
YouTube Videos Promote Software Cracks With Lumma Stealer
Pesquisadores descobriram uma ameaça à segurança cibernética que atinge usuários por meio de vídeos do YouTube. These videos offer pirated software but are being…
Two Adobe ColdFusion Vulnerabilities Exploited in The Wild
Two vulnerabilities in Adobe ColdFusion are exploited in real-world attacks, a Cibersegurança & Agência de segurança de infraestrutura (CISA) avisa. Both issues…
Tortilla (Babuk) Ransomware Decryptor Available
Em janeiro 9, 2024, Avast and Cisco Talos announced the release of a free decryptor for one of the Babuk…
OAuth2 Session Hijack Vulnerability: Details Uncovered
Uma exploração sofisticada direcionada ao sistema de autenticação OAuth2 do Google foi descoberta pelo ator de ameaça Prisma. This exploit leverages undocumented functionalities within…
xDedic Marketplace Members Detained In International Operations
O infame mercado xDedic, known for its illicit trade in compromised computers and personal data, foi efetivamente desmantelado. 19…
Fake Ads on Facebook Promote Scam AI Services
Facebook has been hit by a wave of fake ads…
FIN8 Updated Sardonic Backdoor to Deliver Noberus Ransomware
FIN8, um grupo infame de cibercriminosos, has updated its backdoor…
Citrix and Adobe Vulnerabilities Under Active Exploitation
A Citrix conseguiu corrigir uma vulnerabilidade de dia zero, while Adobe…
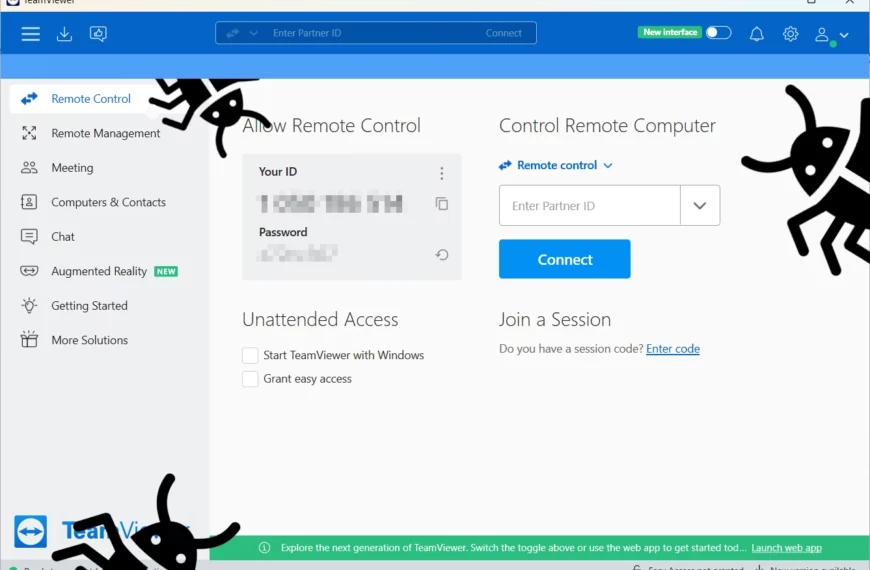
Trojanized TeamViewer Installer Spreads njRAT
Threat actors reportedly started using fake TeamViewer to distribute malware.…
Hundreds of Military and Intelligence Agencies Uploaded Data to VirusTotal
An employee of the Google-owned platform VirusTotal accidentally uploaded a…
WormGPT Helps Cybercriminals to Launch Sophisticated Phishing Attacks
SlashNext noticed that cybercriminals are increasingly using generative AI in…
US Military Emails Leaked Massively Due to the Typo
Email letters sent to the US military addresses ended up…
Microsoft “nOAuth” is Vulnerable to Simple Email Spoofing
Em junho, pesquisadores revelaram uma vulnerabilidade no Azure Active Directory…
American Airlines Hacked by Cl0P Gang, MOVEit Involved
American Airlines, a maior companhia aérea dos EUA, parece…
Trojan:Win32/Randet.A!plock – What is That Detection?
Detecções em massa de cavalos de Tróia no Windows Defender:Win32/Randet.A!plock preocupa as pessoas. Are the…
Microsoft CVE-2023-36884 Vulnerability Exploited in the Wild
Em julho 11, 2023, Microsoft published an article about addressing…
Researchers Found BlackLotus UEFI Bootkit Sources on GitHub
O código-fonte do bootkit BlackLotus UEFI, que foi…