Pontas & Truques
Data Breach & Data Leaks
Data leaks and Data Breaches are very similar phenomena with a slight difference in the principle of action. It was…
Virus:Win32/Grenam.VA!MSR
Virus:Win32/Grenam.VA!MSR é um tipo de malware que pode entrar furtivamente no sistema e estabelecer conexões remotas. Ele permite que invasores…
UsoClient.exe
The UsoClient.exe process is one of the system components of the Windows operating system that is part of the Update…
Broom Cleaner App (Virus Removal)
Broom Cleaner is an unwanted program that at first glance seems to be a safe tool for cleaning and optimizing…
RegAsm.exe
O processo RegAsm.exe é um componente importante do sistema operacional Windows associado ao .NET Framework. Este utilitário é…
RDP Honeypot Was Attacked 3.5 Million Times
Com aumento do trabalho remoto, IT teams use remote access tools…
Third Party Data Breach: Definition and How to Prevent It
No cenário digital de hoje, data breaches have become an alarming…
Beware of Vacation-Related Scams: 4 Most Prevalent Types
Email scam actors constantly try to pick a better disguise…
BlackCat Ransomware New Update Boosts Exfiltration Speed
BlackCat ransomware continues to make a fuss globally for the…
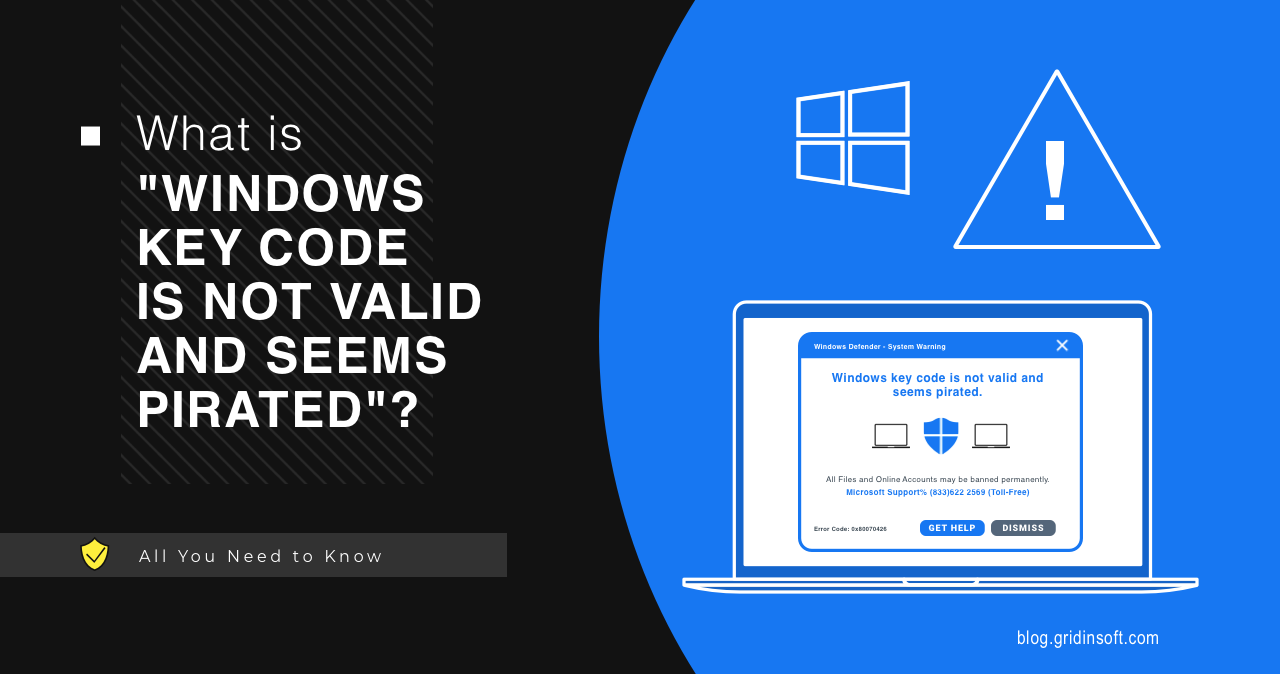
What is “Windows Key Code Is Not Valid And Seems Pirated”?
Windows Key Code Is Not Valid And Seems Pirated appears…
How to Defeat Insider Threat?
No mundo digital atual, organizations face more risks than…
Conti Ransomware Heritage in 2023 – What is Left?
Grupos de ransomware vêm e vão, but the people behind them…
What is Business Email Compromise (BEC) Attack?
Ataque de comprometimento de e-mail comercial, ou em breve BEC, is a relatively…
DDoS-For-Hire Services Used by Hacktivists in 2023
Most people think you must be a hacker to participate…
US Authorities Warn of Disaster-Related Scams
Após desastres naturais e condições climáticas severas, there is a higher…
ChatGPT Causes New Wave of Fleeceware
A inteligência artificial é um dos avanços mais significativos na…
Oneetx.exe – What is that process? Oneetx Removal
Oneetx.exe é um processo malicioso, related to Amadey dropper malware.…