Pontas & Truques
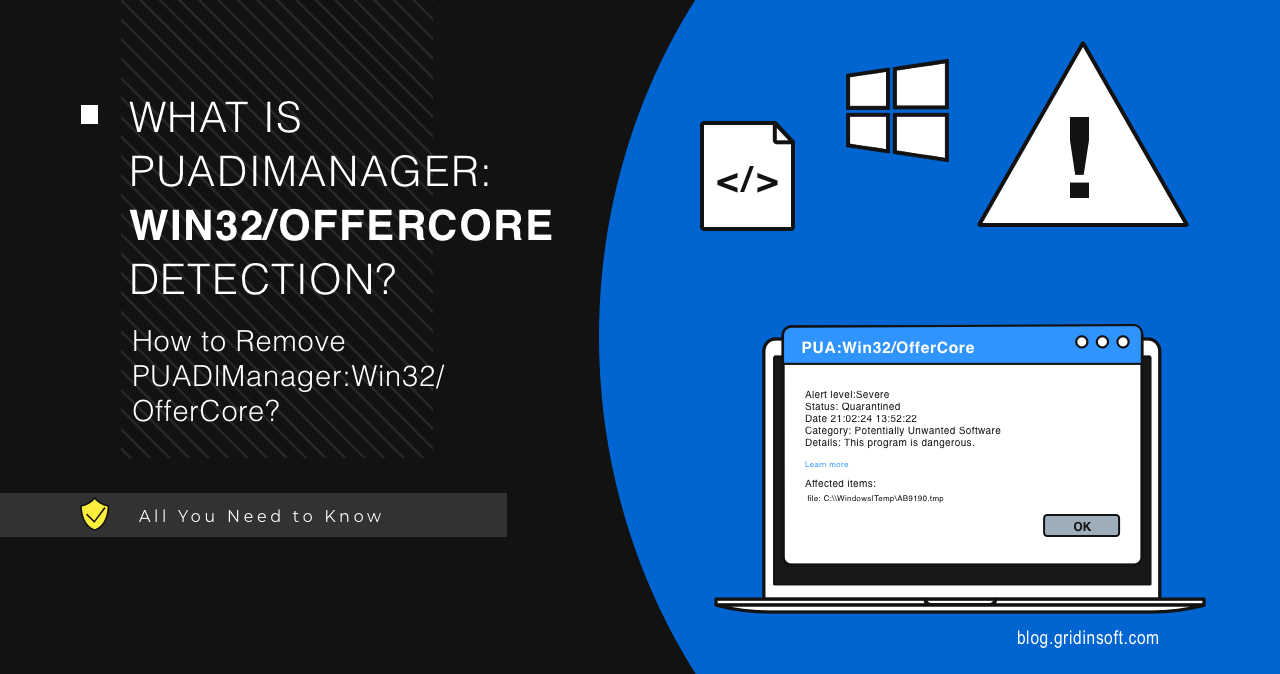
PUADlManager:Win32/OfferCore
PUADlManager:Win32/OfferCore é uma detecção do Microsoft Defender relacionada ao software incluído, specifically to a piece of code that is used…
WinRing0x64.sys Process – What is It? Can I Delete?
WinRing0x64.sys é um driver de baixo nível usado por aplicativos específicos. O arquivo não é malicioso, no entanto, but malware can…
SearchHost High Memory, CPU & GPU Troubleshooting
SearchHost é um processo responsável por indexar o menu Iniciar e os arquivos de pesquisa do Explorer no Windows 10/11. It allows you…
What is Sihost.exe? Windows 10/11 Guide
Sihost.exe é um processo crucial em segundo plano no Windows 11/10 that governs essential features like the context menu and action center.…
Vmmem High Memory and CPU Usage
Vmmem, abreviatura de “Virtual Machine Memory,” is a process that indicates the resource utilization by virtual machines on your system.…
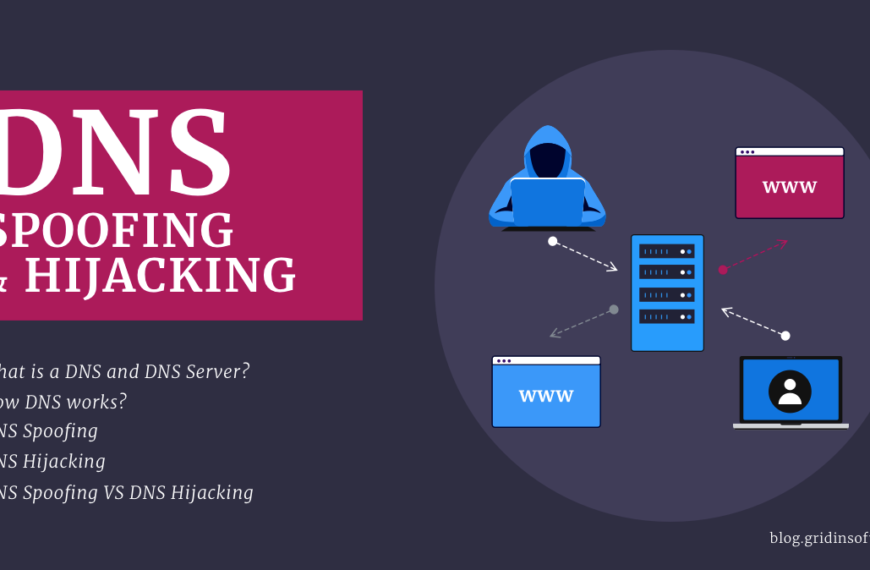
DNS Spoofing VS DNS Hijacking
Domain name services are an essential part of our IP…
6 Popular Types of Hackers: Protection Tips in 2022
A internet nos deu muitas coisas maravilhosas: casas inteligentes,…
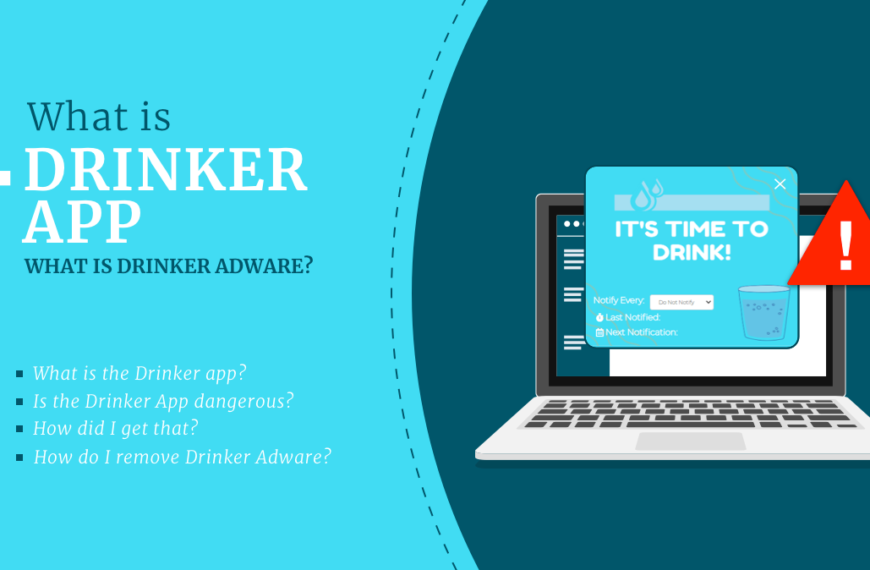
Drinker App – what is Drinker Adware?
The Drinker app is another example of a malicious program…
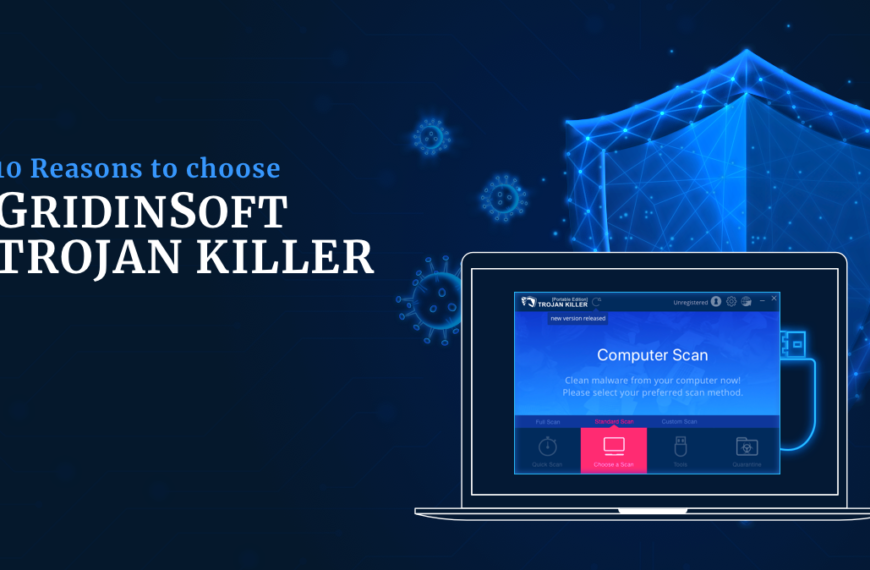
10 Reasons to Choose GridinSoft Trojan Killer
We used to think of anti-malware software as a program…
Healthy App (HealthySoftware) – What is Healthy?
Healthy App seems to be the companion of the other…
Strength Adware – What Is Strength App?
Adware de força, um novo malware publicitário, began appearing on users’…
Methods Hackers Use to Infect You Ransomware
Ransomware hits the headlines almost daily. And most incidents target…
Can Someone Track My Device When Location Settings Off?
Qualquer smartphone já possui serviços de rastreamento de localização integrados. No…
How To Know If Your Phone is Hacked?
Se o seu telefone parou de funcionar corretamente e começou a mostrar sinais óbvios…
Spam Phone Calls Revenge: Prevent Spam Risk Phone Calls
As estatísticas mostram que uma média de 1,900 spam calls are…
How to Stop Spam Texts: Tips to Deal With Fake Text Message
The spam texts can include spam emails and spam calls.…
“Your Account Has Been Locked”: Top 5 Signs of a Phishing Scam
The topic of our article will be how to understand…