
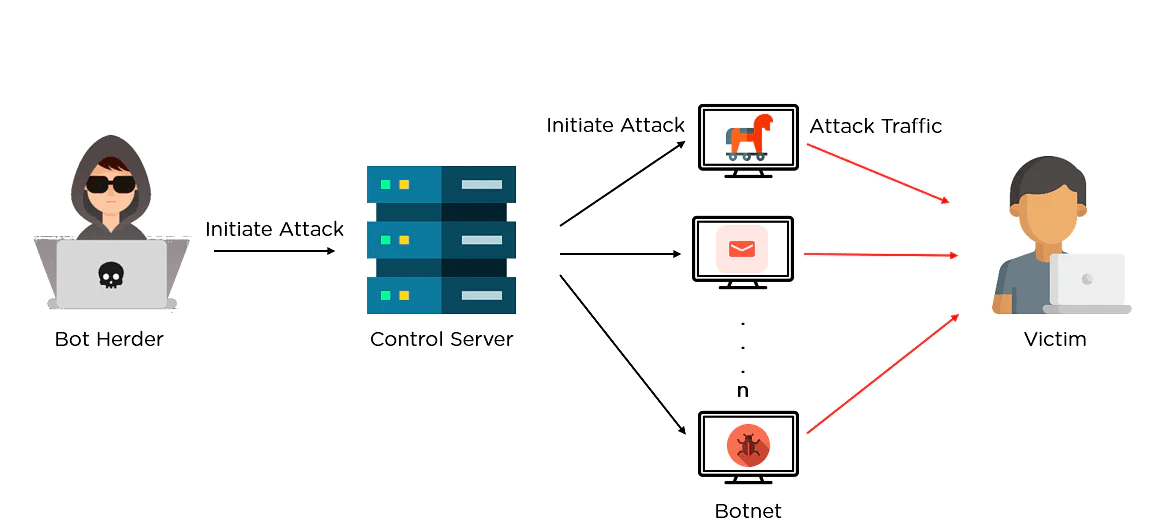
What is a Botnet?
The first thing you need to know is that cybercriminals are not the only burglars who may need a botnet. Often, botnets launch a spam campaign on someone’s page on social networks or do it under someone’s video on YouTube. Of course, both cybercrimes and spamming are unwanted, but the latter is usually rated as a joke or petty dirty trick.
All botnets are different but have a common thing - software that unites the computer into a single network. Usually, for this purpose, botnet creators use backdoor viruses. Of course, they may use any other virus which can modify the networking settings and grant remote access - remote access trojans and stealers, for example. But statistics show that backdoors are preferred - maybe because they are designed for this purpose.
Through the backdoor, crooks change your system settings and networking configurations. They add a specific connection to their command server, use the console command, disable your antivirus, and, finally, download the particular toolkit, which allows them to “wake” your computer and force it to act as they want.
Read also: SmartTube YouTube Client Hacked: Your Ad-Free TV App Just Became a Botnet
Why do cyber cybercriminals need a botnet?
As you read, botnets are called to conduct the spamming activity. All DDoS attacks and effective spamming campaigns are made with the use of botnets. The network, consisting of fully-controlled computers with a centralized control center, is highly effective. Just imagine - you have an army of 100% controlled by you, and you pay nothing to manage all of them - only usual Internet bills. Yes, on Darknet, you may find offers to rent a botnet, but often, these networks are used by the hackers who created them.
The exact purpose of the attacks, performed with botnets’ help, is profit, committing revenge, or creating an illusion. While botnet-based attacks’ first and second reasons can easily be understood, “creating the illusion” must be explained.
Some political parties or opinion leaders sometimes get into a situation when they need to ensure their audience that many people support their opinions. People sometimes make conclusions based on the opinions of other people. However, they rarely think that the “crowd” they see and follow may be illusionary. Botnets are “hired” by unscrupulous mass-media companies or opinion leaders to create an illusion that many people support, for example, the following legislation changes or government changes, which are implemented without democratic voting.
Botnet activity in 2026:
- KimWolf Botnet Hijacks 1.8M Android TVs for Massive DDoS Attacks
- SmartTube YouTube Client Hacked: Your Ad-Free TV App Just Became a Botnet
- GorillaBot: Advanced Mirai Variant Targeting IoT Devices with Enhanced DDoS Capabilities
- New FritzFrog Botnet Sample Exploits Log4Shell and PwnKit
- NoaBot Botnet: The Latest Mirai Offspring
- InfectedSlurs Botnet Exploits Zero-Days to Spread Mirai Malware
- DarkGate and Pikabot Copy the QakBot Malware
- IPStorm Botnet Stopped by the FBI, Operator Detained
How can I understand that my computer is a part of botnet?
Hackers who created botnets have no reason to ensure that a specific user whose PC is in the botnet has already detected that he is hacked. When they have thousands of computers in their network, losing a single PC or even ten ones will not significantly affect them. They may start botnet activity even when you are using your computer. Hence, any strange activity among the listed below is a reason to scan your computer for possible backdoors. Here are the typical signs which indicate that your PC is a part of a botnet:
- The mouse pointer moves autonomously;
- You can see the console windows opening chaotically;
- A browser window opens without your intention;
- You see the 404 error when trying to open the websites, and you can reach this site from another device;
- For laptops: your battery begins uncharging much faster than usual, without any updates in software or hardware or changes in the program you usually run;
- For users with metered connections: traffic is consumed extremely fast by the app you did not use.
Read also: GorillaBot: Advanced Mirai Variant Targeting IoT Devices with Enhanced DDoS Capabilities
At least two of these signs are enough to consider that someone else is using your computer. Don’t panic - crooks who added your computer to the botnet are likely not interested in your data or other sensitive information. All you have to do is to launch anti-malware software, perform the scan and remove the threat. Although the virus can suspend the Microsoft Defender, it can barely disable third-party security tools.
How can I protect my system from turning into a part of a botnet?
It is tough to predict from where the backdoor virus will try to attack your system. Of course, botnets are created not only with backdoors; as mentioned, RATs and stealers are also in this party. Nonetheless, even system administrators can create only passive barriers against viruses. They will be effective until you open the enormous gate for any type of malware - the web browser.
To make your system protected, you need to use anti-malware or antivirus software with a proactive protection function. Security tools with this feature scan the activity of each running application and will detect malware by its behavior. Proactive protection is the most effective solution against backdoors. GridinSoft Anti-Malware is a security tool that can offer you this feature.
